“Hidden Wiki is back,” “Wiki crashed,” “What is the Hidden Wiki?”
You might be asking yourself what the fuss is all about. So now we get to the facts.
The Hidden Wiki was founded back in 2007 as a simple directory for .onion websites on the Tor network. You might think of it as the Yellow Pages of the dark web. Or an evil twin of Wikipedia if you like.
Interestingly, the original Hidden Wiki had more lives than a cat. How? First, in 2013, an unknown hacker hacked and took it down with claims that he wanted to end child sexual exploitation in the deep web. The site came back. Then, law enforcement shut the original one down in 2014 in an operation dubbed Operation Onymous. BUT! It didn’t stay dead. New versions keep popping up like a hydra. Wondering what is Hidden Wiki URL is now? The answer is there is none (the most recent self-claimed lineage is Hidden.Wiki).
The Hidden Wiki has evolved from a specific website into a concept that people seek out when exploring the dark web. Today, dozens—if not hundreds or thousands—of sites use the name “Hidden Wiki.” This proliferation is precisely why you shouldn’t trust any of them. So why do people still search for it long after the original went offline? The answer is simple: it served as the de facto homepage for the dark web, and “Hidden Wiki” is the perfect name for such a resource.
This exact confusion – not knowing which directories are safe or compromised – creates serious security risks for users. It’s precisely why we created OnionWiki: a safe, regularly updated dark web directory you can actually trust.
Below, we first feature a quick list and then details about good Hidden Wiki alternatives, top dark web sites for 2025, and break down what you can expect from these directories and sites.
Dark Web Links at a Glance
Below you’ll find a quick list of all the popular onion sites and information on whether any have been shut down.
Hidden Wiki Alternatives and Directories:
- Dark.site: http://darklcdkooakzfpfef2bpo2yzjgeh3csdxgv6usiw223s7ay2ghdgnad.onion
- Dark.fail: http://darkfailenbsdla5mal2mxn2uz66od5vtzd5qozslagrfzachha3f3id.onion
- OnionDir: http://oniodtu6xudkiblcijrwwkduu2tdle3rav7nlszrjhrxpjtkg4brmgqd.onion
- The Dark Lair: Offline, defunct
Marketplaces:
- Awazon Market: awazone7gyw54yau4vb6gvcac4yhnhcf3dkl3cpfxkywqstrgyroliid.onion/auth/register_now
- Vortex Market: https://vortexgayswedenw5odpj3fv7ddjvywfpoc3hsjeonpvic6g5yf3zmqd.onion/
- WhiteHouse Market: Defunct
- DarkMarket: Offline, shut down by the admin
- Versus Market: Offline, shut down after a hacker leaked a critical security flaw
Darknet search engines:
- OnionFind: http://ofinde3b67voi7xiq3qflof2mwriwngicd7glwvf3bclgdgcjfozlzqd.onion/
- Ahmia: http://juhanurmihxlp77nkq76byazcldy2hlmovfu2epvl5ankdibsot4csyd.onion/
Forums and Communities:
- Tenebris: http://tenebrispoyfrcup4k24lciwrh4gc5735hmld4dweq7his7zh423opqd.onion/
- Dread: https://dreadytofatroptsdj6io7l3xptbet6onoyno2yv7jicoxknyazubrad.onion
- The Hub: http://thehub7xbw4dc5r2.onion
- DarkNet Avengers: Offline, seized by the authorities
Email and Messaging:
- ProtonMail: https://protonmailrmez3lotccipshtkleegetolb73fuirgj7r4o4vfu7ozyd.onion
- Ricochet Refresh: https://www.ricochetrefresh.net
- Sigaint: Offline, defunct now
Hosting and Development:
- OnionShare: http://lldan5gahapx5k7iafb3s4ikijc4ni7gx5iywdflkba5y2ezyg6sjgyd.onion
- Daniel’s Hosting: Offline, shut down permanently after a hack
- Tor Project: http://xmrhfasfg5suueegrnc4gsgyi2tyclcy5oz7f5drnrodmdtob6t2ioyd.onion/onion-services/setup/index.html
Whistleblower Platforms:
- SecureDrop: http://sdolvtfhatvsysc6l34d65ymdwxcujausv7k5jk4cy5ttzhjoi6fzvyd.onion
- GlobaLeaks: https://www.globaleaks.org
- StrongBox: Offline, defunct
Crypto and Escrow Tools:
- Wasabi Wallet: http://wasabiukrxmkdgve5kynjztuovbg43uxcbcxn6y2okcrsg7gb6jdmbad.onion/
- BitBlender: Offline, shut down after a potential exit scam
- EscrowBay: Offline, defunct
Note: Detailed platform information about all and more is covered in the following sections.
Alternatives to Hidden Wiki

We have many routes to the dark web. The Hidden Wiki isn’t the one and only. These other alternatives still serve similar purposes: navigate, organize, and present .onion links differently.
Dark.fail – Popular Onion Service Monitoring
Dark.fail has established itself as one of the more trustworthy alternatives to standard Hidden Wiki-type sites. Their focus on curation and regular updates helps them stand apart from the typical disregard for curation, or as they say, letting the links rot.
The site follows a community verification structure, resulting in active users and moderators who minimize scam links and links that have turned malicious. Users report when links are dead or turn malicious, and moderators respond quickly by removing the entry.
What adds to the value of Dark.fail is its focus on security warnings. They make an effort to warn users about phishing sites and scam links. They even provide context for the warnings, so users can determine which sites are worth the risk of using.
Dark.site – Easy to Use Onion Service Monitoring
Like the one just above it, dark.site, monitors onion sites and services. The only difference is Dark.site seems more strict and choosy when it comes to listing dark web sites. You will see less websites on it compared to any other similar website. What most people enjoy is the fact that is has an interface that is straightforward and easy enough for a new user to get it.
The simple, uncluttered interface is cleaner and more streamlined than other Hidden Wiki-style pages, with more accuracy than coverage. While there may be less total links, the links look more likely to not only work, but also be legitimate.
OnionDir – A Minimalistic Privacy-focused Approach
OnionDir is focused on protecting user privacy while providing minimal tracking/logging of user behavior. It is a highly minimalist interface that loads quickly on Tor and does not offer additional features that would threaten privacy. There is no tracking, no analytics, and no data collected beyond what is necessary to provide the directory.
The listings on this site may not be as broad as other directories, but they focus on the vetting process over quantity of links. Typically, the links on the site are reliable and of a higher quality. There may be fewer total choices, but you can be more confident in the links that are provided. This kind of user typically pairs OnionDir with other listings so that they can get more breadth of coverage while maintaining a privacy-focused browsing experience.
Why Our Site, OnionWiki, is Better: Up-to-date, Secure, and No Tracking
Within the alternatives presented, our directory offers some different and better features for navigating the dark web safely.
We update our listings more regularly than most directories, continuously checking and removing malicious or outdated links at a higher rate than everyone else. This reduces the possibility of experiencing scams or broken sites.
We check links more than directories, which only check user submissions. Our team checks and clicks on links (with all precautionary measures taken at our end, of course), and thus takes a quality check over sheer quantity.
We provide descriptive information and safety recommendations for each link. This is an informative entry for readers as opposed to solely putting URLs without any context or information.
Lastly, unlike others, we only add curated links and do not allow user submissions without a consistent review process. This confirms that links are inspected, thus users can surf safely (we ensure that to the best of our abilities).
The Best Dark Web Sites (Top 2025 Links)

Let’s talk about what you’ll actually find on the Hidden Wiki. These categories represent the most common types and onion sites that people look for.
Marketplaces
The dark web marketplaces are likely what most folks think of when they think of the Hidden Wiki. These marketplaces operate in much the same manner as a normal e-commerce site, except for their emphasis on privacy and anonymity (because of the type of services and goods sold on them). The landscape of these markets changes constantly. For an in-depth, regularly updated analysis of the top players, their security features, and community trust levels, check out our dedicated guide to the best dark web marketplaces.
Below, we list the top 4 darknet marketplaces:
- Awazon Market is a dark web marketplace that has rapidly gained popularity by offering anonymous e-commerce services. The market emphasizes security, featuring mandatory vendor screening with extended verification, as well as a built-in dispute resolution system (where admins jump in for resolution). Awazon has positioned itself as a successor to the popular AlphaBay market, which was shut down by authorities in July 2023 after efforts that started in 2017.
- Vortex Market operates as a hidden online bazaar on the darknet. The marketplace itself offers a wide range of products. While some listings are for legal goods, many others occupy legal and ethical gray areas, which primarily drives the market’s notoriety. Like Awazon, it uses cryptocurrencies like Bitcoin to process payments that are difficult to trace. At the same time, strong encryption secures all communications and financial data, creating a secure environment for its users.
- WhiteHouse Market has built a solid reputation through extended vendor verification and a user-friendly interface. They use escrow services to hold funds until transactions are completed successfully, plus PGP encryption for all communications. This significantly reduces the chances of getting scammed.
- DarkMarket stands out for its sheer size – it’s one of the largest platforms by transaction volume. What makes it interesting is anti-DDoS protection and robust encryption protocols that keep the site accessible even when under attack (which is a norm on the darknet).
Dark web marketplaces are always changing their ways to stay ahead of law enforcement and technical obstacles, like for example, their mirror URLs keep changing. That is generally why directories like Hidden Wiki (now, this website, OnionWiki) are super useful for providing current portals for access.
Forums and Communities
The social aspect of the dark web holds equal importance to the commercial aspect. Forums are a venue where users share information, discuss security measures, and build community. Below we list the top dark web forums:
- Tenebris: This darknet forum is so well designed that you might become addicted to it. Like mainstream forums such as Reddit, it has communities (replacing Reddit’s subreddits), where you can post and ask about anything from dark web markets to tips and tricks to entertainment.
- Dread is really just the Reddit of the dark web (as it name suggests). Threads are open discussions about darknet security measures, market announcements, and other general dark web topics. The community heads the moderation of the material presented on Dread, reducing scams and misleading information—this makes it a more reliable source of current information.
- The Hub is more focused on education and community support, with extensive guides and guides presented for both new and more experienced users. You can find everything from how to review vendors to suggestions on OPSEC (Operational Security) for their activity. The Hub is essential for even those trying to understand best practices.
- DarkNet Avengers is a hacker and activist-oriented forum, discussing topics like censorship resistance, privacy tools, and digital rights. The discussion trends tend towards the tech and political ends of the spectrum. These forums provide the dark web with an additional layer of social fabric while also carrying overall community interests, like reporting scams and related technical issues in online communities.
Email and Messaging Services
Communication security is absolutely critical on the dark web. Regular email services aren’t designed with the level of privacy that dark web users need.
- ProtonMail’s onion service provides the same encrypted email that millions rely on around the world, but now, anonymously, via the Tor network. This twin function keeps your messages safe from eavesdropping and censorship, making it crucial to activists and journalists operating in hostile countries.
- For real-time talk, Ricochet Refresh provides a different option: peer-to-peer encrypted, decentralized chats using Tor and no central servers. This makes surveillance far less of a risk, as there is no central point that can fail or collect data on the user.
- Sigaint is another individual encrypted email service targeting privacy advocates and whistleblowers. The focus here is simplicity and tight security so that even not particularly computer savvy users can access the service.
These communication methods provide the basis for intimate chats and discussions in high-risk environments where typical communication methods you might have relied on are less secure.
Hosting and Development
Running a website or continuing to share files securely from the dark web requires a specialty of tools and services.
- OnionShare remains an open-source resource that grants safe file sharing and anonymity on Tor. Activists, journalists and many other good guys use it to distribute sensitive documents. Why? It does not work with a central server or demand for an account.
- Daniel‘s Hosting not only specializes in anonymous web hosting optimized for Tor but also provides secure environments with good DDoS protection as dark web sites generally are targets for attack from several directions (competirors, governments, all).
- The Tor Project‘s official onion website provides access to secure Tor Browser downloads and developer resources, allowing users to access and contribute to the Tor ecosystem with assurance that these downloads have not been tampered with.
These platforms are also the technical backbone that makes the dark web possible. It would collapse without reliable hosting and development tools.
Platforms for Whistleblowers
One thing all of these have in common is “protecting sources of information.” Whether you’re sharing with renowned organizations or journalists, these Whistleblower resources come in handy.
- SecureDrop is a secure, encrypted system used by many large media organizations to provide a whistleblower portal to use to submit information without risking their identity. The system is designed to have no logging and traceability, which protects the source even if the receiving organization is compromised.
- StrongBox also includes robust features, including metadata stripping and greatly expanded encrypted messaging, which add yet another safeguard for sensitive communication. These tools are an essential infrastructure for human rights efforts and investigative journalism in places where speaking out against authorities and regimes can have serious consequences.
- GlobaLeaks is an open-source platform used by media organizations and NGOs to build submission portals that can customize the processes for submissions. The focus on anonymity and decentralization is especially useful for organizations that work in oppressive environments.
Escrow and Crypto Tools
One of the primary concerns on the dark web is financial privacy, and these tools aim to reduce risks when sending financial information.
- EscrowBay is a dedicated escrow service that specializes in dark web transactions. They hold funds in secured transactions until both buyers and sellers confirm to each other that they are satisfied with the transaction, again, substantially mitigating risks of fraud.
- Wasabi Wallet is a wallet for Bitcoin that facilitates CoinJoin mixing, which obfuscates transaction trails. As a result, it becomes much harder to link Bitcoin transactions back to users, thus improving your anonymity and financial privacy.
- BitBlender offers cryptocurrency mixing services that pool multiple users’ coins together to further anonymize origin and destination. The service can be likened to shuffling cards as a way to describe moving funds without needing a clear transaction path. When you send your money to BitBlender, you will receive a different coin back with coin yields that are shuffled with funds from other users. As such, it breaks the path of your original coin from origin to destination.
All of these tools substantially mitigate risks when exchanging financial information on the dark web, while being an essential component in order for the ecosystem to operate safely and effectively.
What is the Hidden Wiki?

The Hidden Wiki is like your GPS for the dark web. If you are driving in a new city, you will most likely want directions. This is similar, except instead of locating the next coffee shop, you are wandering around a completely different side of the internet. If you’re new to this entire concept, our complete guide to the dark web explains the layers of the internet and where the dark web fits in.
An All-Inclusive Directory of .onion Links
Interestingly, the Hidden Wiki functions exactly like those old-school web directories from the 90s – you know, before Google took over the world. It organizes .onion links into neat categories: marketplaces, forums, search engines, email providers, and more.
Why is this important? It’s simple! Mainstream search engines such as Google cannot access .onion pages. They are invisible to regular crawlers. Thus, if there were no directories like “the Hidden Wiki,” finding .onion links would be like searching for a pin in a haystack with blindfolds.
A Facilitator for Safe Tour Across the Dark Web
The dark web feels like the “Wild West,” especially for newcomers. Nothing is 100% trusted, and danger is expected too. This is where the Hidden Wiki becomes your best bet. It stands in like a filter, which provides a verifiable list of links. What’s more! It informs users about potential scams.
Now don’t get the wrong idea. This directory is not some magical security blanket to safeguard you from anything. It does, however, minimize danger by providing descriptions of sites and displaying known troublesome links. For those that are new to Tor, it’s a much safer place to start than clicking random .onion links from some forum.
Wait! Exercise Caution
Even though you have hundreds of these protections, being vigilant can’t be overlooked. Remember the internet’s golden rules!
don’t give out personal information,
don’t click on strange links,
Use tools to complement your privacy, for example a VPN (we recommend using NordVPN as it has a strict no-log policy and offers fast speeds).
The dark web may provide some anonymity, but that same anonymity also provides cover for people up to no good. The dangers here are often hidden and can extend far beyond your computer screen. To fully grasp what you might be stepping into, our guide on the hidden cost of the dark web is an essential read.
How Does the Hidden Wiki Work?
Nothing ambiguous happens here. It basically gathers .onion links for visitors and sorts them in appropriate manner. So, navigation becomes easy. That’s it! But let’s dive deeper.
What the Hidden Wiki Contains
The Hidden Wiki is a type of curated directory of .onion websites that you can only get to through Tor. This directory is organized in multiple sections and contains a variety of services and communities.
You can find links to common marketplaces where people buy and sell items anonymously. Forums and discussion boards for users to exchange information, discuss subjects, and exchange tips on security. The directory also has important privacy-oriented services. We have providers of encrypted email, platforms for anonymous messaging, and programs for cryptocurrency. What’s the aim? To foster your anonymity as you perform transactions.
What’s more! You can locate hosting for people who want to run their own .onion sites. And, you may even see some whistleblower platforms that facilitate secure communication and file sharing! Ultimately, it is a type of parallel internet that puts privacy first.
Reasons People Use the Hidden Wiki
People use the Hidden Wiki for a variety of reasons, though they may not all be as you think. The most obvious is navigation. The dark web can be difficult to navigate, and having a centralized directory can make things easier.
Privacy is a large part of the user base. In fact, it’s the number two reason people use Hidden Wiki. The fact that you connect to the Tor Network and then access this directory, nothing about your identity or activity is jeopardized. “No surveillance” is one way you can think of it. Those under government radars or reporters steadily working with critical info and activists have this common reason for using Hidden Wiki.
Another “why” is evading censorship. Normally, censorship blocks certain content, services, and information from selected regions. With this director, one can bypass this block and source as much information as needed. Most individuals reside in regions where the web is under heavy censorship; using this directory is how they can source information and communicate with ease.
Constant Link Verifications and Updates
Here’s something most people don’t realize: the dark web changes constantly. Sites disappear overnight, URLs change without warning, and new scams pop up regularly. Maintaining an accurate directory is like trying to map a city where the streets keep moving.
A Hidden Wiki like OnionWiki stays relevant through community effort. Moderators and users are always reviewing links, deleting broken or malicious links, and adding new, trusted links. It’s a losing battle against the continuous degradation, but it is what makes a directory usable, instead of just a graveyard for broken links.
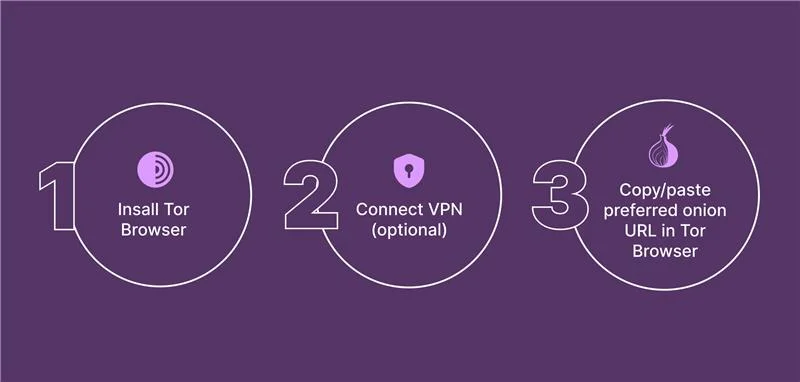
Accessing the Hidden Wiki and Dark Web
Accessing the Hidden Wiki is not difficult if you take proper precautions to keep yourself safe from prying eyes.
Install Tor Browser
Your access to the Hidden Wiki starts with the Tor Browser. Download Tor for your device. That’s a secure browser and not your normal internet browser like Chrome or Firefox. It is a browser designed to send your web traffic via the Tor network to anonymize your connection. If you are a Firefox user, you might find it relevant as the Tor browser’s user interface is based on Firefox.
Here’s how the Tor network works: instead of bringing you directly to a website, your internet traffic goes through several volunteer-operated servers across the globe in a zig-zag fashion. Whenever you connect and are directed to a different server in the Tor Network, your data is encrypted, and your IP address is concealed.
This makes it almost impossible for someone to backtrack your activity back to you. Make sure you ONLY download the Tor Browser from the official Tor Project site. This is important because there are fake copies of the browser floating around with malware or altered in such a way that your activity can be traced.
The Tor browser is available in Windows, Android, Mac, and Linux. It only takes a couple of minutes to install, like any other software you download. Once you open the browser, it connects you to the Tor network. This initial connection may take some time based on your internet speed and the health of the Tor network at that time.
The Tor Browser may look like any other browser you use, but it is configured out of the box to provide a high standard of privacy. The Tor Browser will stop trackers and attempt to protect you against fingerprinting techniques that websites can use to identify their users. Be aware that using Tor will typically take longer than your regular browsing session, since your data hops from place to place.
Enhance Security with a VPN (Optional)
You can use Tor and a VPN in conjunction to invoke another layer of security for your anonymity, as many privacy-minded individuals recommend. VPNs increase security by hiding IP addresses, creating encrypted data connections, which enhances online privacy.
When you use it with Tor, a VPN service will encrypt your web traffic before it even goes into the Tor network. That way, your ISP (internet service provider) won’t even know whether you’re on Tor. What’s more! The first Tor relay won’t even know what your original IP is. This is like a two-in-one disguise.
To get the best out of this, use a VPN with a strict zero-logs policy as well as ideal privacy tools. You should not sign up for a free VPN service – free VPN services often make their money by selling your data or showing you ads, which defeats the purpose of using privacy tools. We recommend that you only choose a premium VPN like NordVPN.
Be sure to run your VPN prior to using the Tor Browser. That way, you will first run your traffic via VPN’s encrypted tunnel, and then through your Tor network.
Although this will slow your internet connection even more, it’s safe to say that many users feel the trade-off for enhanced security is worthwhile. Doing so hides your Tor usage from your Internet Service Provider and helps protect against any compromised Tor entry nodes, as that adds an extra layer of encryption before your internet traffic enters the Tor network.
Pasting the .onion URL in Tor Browser
After you get Tor running (along with your VPN if you use one for added security), getting to the hidden wiki will just require you to input the .onion link into the address bar.
.onion addresses look nothing like normal websites. They look like a long string of random numbers and letters, like when one of your cats walks across the keyboard and enters your password. “whoaisduiothasosdopasdncxopi089q7ewklaj.onion” They’re designed for anonymity rather than memorability (or even usability, you can say).
Be very careful copying the .onion link – even one character wrong, and you can end up on an error page or worse, a malicious version of the page that is spoofing the Hidden Wikis or another dark website you wanted to visit. Always check for a valid and accurate URL from a trusted source.
After entering the address and hitting enter, Tor connects to the website through its network. This usually takes a little longer than loading a typical site, so be patient. The extra waiting time is the cost of being anonymous.
An example of a Wiki Link is http://zqktlwiuavvvqqt4ybvgvi7tyo4hjl5xgfuvpdf6otjiycgwqbym2qassd.onion/wiki/ (not working). That long, cryptic .onion address? Exactly! The whole point of a Tor directory like OnionWiki is pretty straightforward: to help you find stuff on the dark web without having to memorize those ridiculously long .onion URLs. And trust us, you don’t want to be typing out 56-character addresses from memory.
So how does one access the dark web from Hidden Wiki?
As always, you should know that some regions disapprove of anyone who visits the dark web for any reason. You should always ensure you are in a location where that is allowed.
That said, here’s what to do:
- Download and set up the Tor browser on your device – macOS, Windows, or your mobile phone.
- Open the browser and copy/paste the onion URL you wish to visit. We’ve listed a lot of hidden services’ direct URLs above. You can also visit a new hidden wiki URL (or one of its alternatives you like) or head to a darknet search engine such as OnionFind to find the site you need.
- Congrats! Click on the .onion URLs on your screen, and you’re into the dark web.
Pro tip: Once you’ve the site URL you think you’ll need to visit often, you can bookmark the site for easier access next time.
Getting onto the Dark Web? Consider These Safety Precautions

For a deep dive into every one of these precautions and more, our how to browse the dark web safely guide is your go-to resource. Want quick tips here? Alright so if one must remain protected on the dark web, then one must be alert and follow the best safety practices. These are nothing new!
Never reveal your real identity or legal data on any site on the dark web.
Use emails that have no connection to you. Not even one of your legal names, addresses, or data should be on that email account.
In fact, adopt a pseudonym if you’re going to live on the dark web.
DONT DOWNLOAD! AVOID WEIRD LINKS!
Why? Thousands, if not millions, of malware and phishing attempts are hanging around. You can’t 100% avoid them. Plus, the dark web is so anonymous, you’d surely break a sweat tracking the attacker. If it’s too good to be legit, RUN!
What’s more! Always check if your Tor Browser has a new version. Run the update if available before going to the dark web. If you check under “What’s New,” you’d see several enhancements and even security patches that can help keep you safe and less vulnerable.
Again, always disable JavaScript when using unknown sites. And avoid using any browser plugins that are likely to expose identifying information.
Avoid using your regular email and payment accounts for any transactions on the dark web. If you need to perform a transaction on the dark web, you should establish and create a separate cryptocurrency wallet and conduct transactions through only encrypted communication channels.
Additionally, stay involved and informed through reputable sources in the community about current threat assessment and trends, and best practices. The dark web environment is constantly changing, and the things that may not have been dangerous yesterday may be dangerous today.
Is the Hidden Wiki “Safe?”
Without a doubt, this directory has good value. Regardless, we are talking about the dark web here so there are risks. Knowing what the risks are can mitigate some of the dangers.
Phishing Clones, Honeypots, and Scam Links on the Likes of Hidden Wiki
The dark web is recognized for containing malicious content, and the Hidden Wiki has its share of issues.
Scam links are ubiquitous; some may serve a fake marketplace and take your payment without ever delivering the product, or some may offer a bogus service that meets results. If you paid for any of those services using a cryptocurrency, there isn’t going back. For the most part, everything operates anonymously, and you will not be able to get your money back.
Phishing clones are worse. These are legitimate sites’ fake copies that steal user login credentials or personal information, and they often look just like the real sites unless you are paying careful attention to the URL.
Honeypots pose the biggest risks. They are also websites created by government agencies or some malicious figures with the apparent goal of identifying and tracking targeted users. Law enforcement activities may include having illegal content or services so the site can entice individuals to incriminate themselves, while then using different methods to attempt to identify visitors.
Since the Hidden Wiki combines links from other sites or forums, these links are often out-of-date or compromised links relating to legitimate sites. Clicking on a link with anything other than an appropriate investigation can be risky.
Tips to Verify Hidden Wiki Links
As any Hidden Wiki site can be an unindexed content hub, it can be prone to misleading or fake links. Safety is paramount, but how can one stay safe? One way is to verify links. Now, before you panic, here are tips to answer your “how?”
First things first, use community-validated sources when it comes to sharing links. And, only use recently updated onion link lists from forums like Tenebris, The Hub, or Dread that are trusted. In these communities, users constantly confirm who is a valid .onion and which ones a scam websites. Visit these threads and share recent feedback and reviews about sites before visiting a particular forum. If a marketplace or service has a lot of complaints or reports around it suddenly, that should be considered a red flag.
If a marketplace or service has a Public PGP key, resources should be used to validate the identity of the marketplace or service. An honest operator will publish PGP signatures to prove they are authentic, and contact persons may often post their PGP signatures if they are truthful and not fraudsters. If it cannot be verified, be suspicious.
Verify links through multiple sources to ensure alignment. If different reputable sources are directing you to different links for the same service, it’s time to be suspicious.
Avoid links that are in unmoderated or random areas (forums, social media), as these links are frequently the most dangerous types of links. Use links from moderated areas where the community actively helps remove harmful links.
Safe Browsing on the Hidden Wiki
Want to make the most of surfing the Hidden Wiki? Then keep these precautions within your reach so you don’t miss any.
ONLY USE Tor’s official Browser for any .onion link. NEVER try to visit .onion sites using your normal browser – Chrome, Safari, Mozilla, whatsoever. The safety these browsers give is nothing like what the Tor Browser does. Plus, the search engine of your browser can’t crawl such links except Tor. So, use ONLY Tor for .onion links.
Disable JS (JavaScript) and any irrelevant extensions you might have. A slight loophole in these features can put your identity at risk. worst-case scenario – they can give the bad actors an entry point to your device.
NEVER download or click on any attached file from sources you don’t know or trust. Malware is rampant on the dark web, and it is very difficult to get assistance if you do fall victim to malware, given the anonymity of the dark web.
Use strong passwords and 2FA. Always set up your accounts with strong and unique passwords. No matter the purpose of that account, this is important. Layer the security with two-factor authentication on platforms that support it. What’s more? Do not use the same passwords for your normal internet activities.
Pay with crypto and use escrows. Crypto fosters anonymity on its own. Use it for transactions on the Hidden Wiki. It also supports escrow, which guarantees safe transactions. Fraudulent intents will likely fail, and you’d get a form of recovery if anything should go wrong.
Be alert. The dark web has security advisories in several communities. You’d find experts in cybersecurity there as well. Follow these key players to stay informed about current trends and threats in the space. For your information, threats are ever-evolving, and to be alert is one prudent way to be on the safest side.
Final Thoughts and Disclaimer
If you must surf the dark web, then you must be cautious and aware. Without a doubt, you’ll find valuable resources like information with censors. You can perform communications that are anonymous and even access services that are privacy-focused.
Yet, you are not 100% covered from consequential risks. Don’t fret! You can still surf this sector safely if you abide by the security practices in this guide.
It’s nothing tasking! Just make sure to confirm links, information, and their sources. Don’t “download” every file that crosses your path, especially from roots you don’t know.
Most visitors ignore these practices. So, we put in more effort to gather reliable information, monitor, and overhaul our directories. That way, there’s minimal risk, and anyone visiting can meet legit sites they can trust.
Notwithstanding, users are solely responsible for whatever they do on the dark web and should adhere to all application regulations and laws in their jurisdiction. Remember, the dark web is ever-evolving, so seeing new threats, fresh schemes, and lots more popping up is expected. As advised, stay vigilant, use updated tools, and more especially, avoid illegal activities.
Disclaimer: While we do the hard work to curate safe and accurate listings, 100% safety, legality, or reliability of these listings are not guaranteed. As a visitor, your safety and compliance are your responsibility. By using these resources, you acknowledge and agree to own up to your actions.
FAQs about Hidden Wiki
The Hidden Wiki is a directory site for .onion links on the dark web. Its work is to assist people in finding hidden services like forums, marketplaces, email services, and whistleblower sites quickly. Also, it’s a safe entry point for those surfing the dark web, thanks to how such a website (we should rather say hub) organizes and categorizes links to sites that a regular search engine cannot crawl.
The Hidden Wiki isn’t a single website (anymore) but a concept for a directory of dark web links that people search for. The original site is long gone, and what you find today under similar names are various unofficial successors and mirrors with varying levels of trustworthiness.
In most countries, finding and browsing through dark web links is not illegal. Despite the popular belief about it, the dark web also includes many valid services that exist only to follow the values of information freedom and privacy. However, some hidden services consist of or help facilitate illegal activities such as hacking services or prohibited drug sales. Browsing the dark web is legal, but using .onion links to facilitate an illegal transaction or activity brings legal consequences.
First, always use the updated Tor Browser and have unique, strong passwords. The second tip is to NEVER disclose personal data. Be sure the .onion links are from legit sources. You can also use a VPN service to layer your security on Tor. What’s more? That’s because good security requires you to complete a whole puzzle. Whenever on such websites, also turn off JavaScript, and do not “download” any form of attachment. Last but not least, common sense is your best friend; avoid clicking on links that seem fishy.
You should always exercise caution and use only the verified link. Otherwise, you could be the victim of a phishing scam, infected with malware, or placed in a law enforcement honeypot designed occasionally to catch bad actors. If you click on a link that you believe is “bad,” immediately disconnect your device from the internet, run a full (extended, not quick) malware scan, and change any password that might have been compromised.
The answer is no. You cannot visit the Hidden Wiki or any .onion site if you don’t have the Tor browser installed. .onion sites exist only on the Tor network, so they will never open in common browsers such as Chrome or Firefox. No matter how many times you try visiting an onion link in Chrome or any standard clearnet browser, you’ll keep seeing the ‘This site can’t be reached’ error message.
