The internet is frequently likened to an iceberg: the surface web (what is indexed by Google) is the tip of the iceberg, the deep web accounts for the massive underwater portion, and the dark web represents the bottom, almost unreachable section. The dark web, which is totally motivated by technology that guarantees anonymity, is a secret ecosystem where (like the deep web) anonymity implies privacy, and privacy implies danger.
This guide will dissect the Dark Web Dangers and Risk, meticulously detailing the ten most critical threats faced by anyone who ventures into this hidden domain.
We’ll explore the true scale of the risk, moving past sensationalism to give you a clear understanding of the disadvantages of dark web exploration and how the anonymous environment, while useful for some, can become a digital minefield for others.
Is the Dark Web Dangerous?

The answer is – yes, the dark web is dangerous; however, it is not uniformly dangerous, it is both widespread and systemic. The dark web is a system built from the ground up on anonymity – no accountability, consumer protection, or safety. The absence of regulation creates a hostile environment for the non-criminal user.
There are three main categories rooted in danger:
Technical Exploitation
The browser used to connect to the dark web (dark web browser), such as Tor, can become the target of exploitation, and malware operating behind the scenes can infect your operating system by visiting dark web sites, which are full of drive-by malware.
Psychological and Legal Harm
To come across shocking, disturbing and/or illegal content is the constant risk of engaging the Dark Web; with psychological harm and possible legal consequences for the content while engaging.
Financial Fraud and Deception
Scams, fake commercial entities, and thieves exist throughout the Dark Web, which exploits anonymity.
With a lack of control from anonymity, maximum criminality becomes possible, as is present on the Dark Web. Therefore, it is only safe to engage the dark web with advanced knowledge and caution.
What is the Dark Web?
The dark web is a section of the World Wide Web that is intentionally hidden and can only be accessed using a special anonymizing software such as the Tor browser.
Deep Web vs. Dark Web
When considering the Dark Web Dangers and risk, it is important to differentiate between two concepts:
Deep Web
The deep web represents 90% of the internet. This category includes content that requires payments through paywalls, subscriptions, private web-based inboxes, and proprietary databases. It is not bad; it’s just not organized by Google.
Dark Web
Conversely, the dark web just constitutes less than 0.1% of the internet. This section is intentionally obscured from normal use, created for end-to-end anonymity, and features both totally legitimate private communications and illegal black markets.
Who Created the Dark Web?
Knowing how it developed helps make sense of what it was developed for. The actual invention of the technology, which is referred to as onion routing, was conceived by researchers at the U.S. Naval Research Laboratory in the mid-1990s.
It was offered to secure U.S. intelligence communications over the internet by layering encryption and routing the traffic randomly through those layers. Later, it was released as free, open-source software (The Tor Project) in order to create a large and diverse set of users, providing some protection to government users.
In other words, the technology was developed for secure communications, but it was conveniently structured for criminal activity.
Why You Should Not Explore the Dark Web without Proper Knowledge

For the average user, exploring the dark web without an extensive knowledge of technical and operational security (OpSec), is like walking into a warzone without armor. Without proper preparation, the disadvantages of dark web engagement increase rapidly.
The risks of this environment are increased because ignorance is not tolerated:
Compromise by Configuration Errors
The trust of anonymity is tenuous. Those who are not tech savvy often make simple errors, like not disabling JavaScript, resizing the dark web browser application (a leak for your screen resolution), or sharing as a surface web user, which links their identity to their session in Tor.
Regardless, one small configuration error will almost immediately de-anonymize you, while exposing your real IP address and location to a threat actor or government agency.
Targeted Attacks
The dark web is full of hackers who are good at attacking targets that are unprotected. Hackers perceive all users who visit the dark web, identifying those who are new or who do not have sufficient security knowledge, as their easy targets.
Attackers use known and unknown exploits against Tor network protections for surface users. In these situations, the bad actor does not need to be in your local area; they can exploit your host device in seconds every time you click without binding it in a properly sandboxed machine, running a secure operating system like Tails, or updating regularly to a patched version of your host operating system.
Financial and Data Loss Is Irrecoverable
Exit scams, fake investment schemes, and phishing attacks primarily target new users for fraud. New users may not have the requisite knowledge to vet any external vendor or safely deal in cryptocurrency, leaving them particularly vulnerable to losing money, with no prospect of recovering their funds or recourse. The environment assumes you are competent and, if you are not, you are prey.
The 10 Major Dangers and Risks of the Dark Web
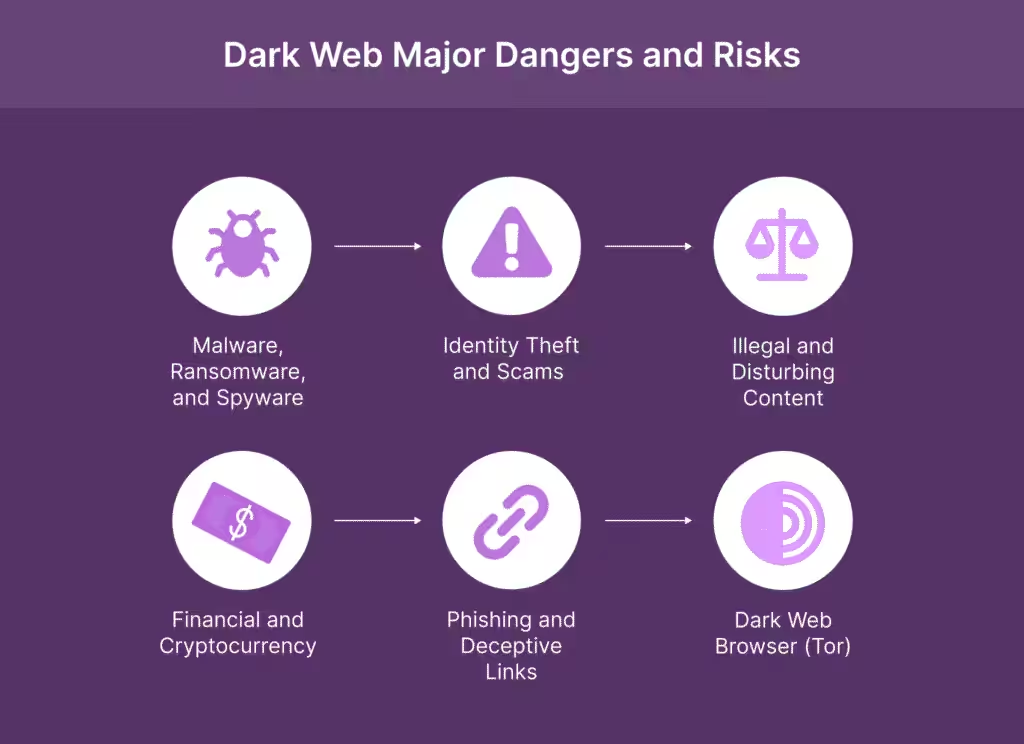
Dark web’s volatility and the absence of regulation materialize into certain high-impact threats.
1. Malware, Ransomware, and Spyware
This is the most common and immediate technical threat. Dark web sites are prime distribution hubs for malware. Cybercriminals can utilize some sophisticated scripts to carry out “drive-by downloads.” By merely visiting a page, malicious code could initiate and take effect. That code could put ransomware on your system (where the ransomware encrypts your system, and afterwards demands payment), keyloggers (stealing your passwords and any financial data), or spyware (monitoring your activity in the background). This danger targets your hardware and data directly.
2. Identity Theft and Scams
The dark web runs on stolen credentials, making identity theft a pervasive Dark Web Danger and Risk. However, the danger goes far beyond purchasing stolen data; it is an economic model based on continuous deception.
When you enter the dark web, you are entering a market designed to steal from you. Criminals set up extremely well-designed dark web sites and marketplaces that are, in reality, complex exit scams, by collecting millions in cryptocurrency for products or services, and then disappearing; they always take the money with them. Additionally, when someone claims to sell services, such as hacking, murder, or counterfeit documents, these claims are from a fraudster.
The fraud relies on the victim’s fear of reporting the crime to law enforcement. They collect the fee and disappear. Even if you are purchasing a legitimate product, you are running a high risk of receiving malware, getting defrauded by an intermediary “escrow” service, or having your personal information stolen during the transaction process. Because anonymity shields both the buyer and the seller, the rule of law is replaced by the law of the scammer.
3. Illegal and Disturbing Content Exposure
The dark web is infamous for hosting Child Sexual Abuse Material (CSAM), extreme violence, and other highly illegal content. Accidental click-throughs and browsing are punishable and very serious offenses.
Numerous sites intentionally leave descriptions vague or promote shocking or violent images for the sake of click-through and to trap the viewers into watching something illegal. Even accidental viewing of something that is not only morally reprehensible, but also carries difficult-to-imagine penal consequences.
Law enforcement targets those who view CSAM, and the simple fact that a user may have buffered or downloaded a temporary folder can be prosecuted as a serious felony. The psychological consequences of illegal exposure can be treated, but may exist and have ramifications for a broader subset of exposure or awareness.
4. Law Enforcement and Legal Issues
The idea that the dark web browser (Tor) provides total security and anonymity is not accurate and is a myth. Various international law enforcement agencies (examples include the FBI, DEA & Europol) are constantly monitoring, infiltrating, and taking down criminal dark web sites.
Law enforcement will often create “honeypot” sites to log and capture IP addresses and activity of any user who clicks the sites. Even engaging with those sites out of mere curiosity could result in your IP address logged in an official honeypot.
This could bring your de-anonymized IP address to the attention of law enforcement who could then document the activity for future investigations, exposing you to serious legal risk where any user activity can sometimes demonstrate potential criminal intent. You risk becoming part of a dragnet operation.
5. Financial and Cryptocurrency Fraud
Beyond simple identity theft, the dark web is rife with advanced financial fraud leveraging the untraceable nature of cryptocurrency. This includes setting up fake investment “opportunities” or services that promise to “mix” or “tumble” your cryptocurrency but simply steal it.
Other risks involve the sale of counterfeit financial instruments, cloned credit cards, and access keys to compromised bank portals. Since all transactions are final and handled via irreversible crypto payments, there is zero mechanism for chargebacks or refunds, guaranteeing loss if the fraud is successful.
6. Phishing and Deceptive Links
Due to the long, complex, and unmemorable nature of .onion addresses, criminals exploit this cognitive weakness to great effect. They create nearly identical phishing sites (known as ‘typosquatting’) for popular marketplaces or services.
For instance, only changing one letter in an onion address could redirect a user to a non-authentic site. Any user that goes to these misleading links is fooled into submitting their information and/or sensitive information, including their username and password, 2FA keys, or cryptocurrency wallet seeds.
Because the very nature of these sites is dependent upon anonymity, reporting or taking down sophisticated phishing sites used for criminal intent, becomes exceedingly difficult to do, allowing it to be an active site catching new victims indefinitely.
7. Vulnerabilities in the Dark Web Browser (Tor)
Although the dark web browser (Tor) has its plus points and is useful, it is not perfect; there may be vulnerabilities in the code of the browser or in the code components which are its basis (i.e., JavaScript). The Tor network is also vulnerable to a Sybil attack or relay attack, where a single adversary controls a sizable portion of the entry and exit nodes.
If the adversary controls both the entry and exit points being used, they may be able to conduct further traffic correlation attacks in order to attempt to de-anonymize the user’s session. This risk is something central, important, and ongoing; meaning users need to frequently keep their software up to date and avoid using risky behaviors, as this could settle data that exposes the system to the boards of things.
8. Exposure to High-Risk Individuals and Communities
By willingly going to dark web forums, chat rooms, or niche market sites, you are intentionally exposing yourself to a community of hostile actors. They are active participants, not passive users.
They are sophisticated bad actors (cybercriminals/hackers/extortionists/etc.) who seek new victims. A simple question posted or a note of confusion will make you identifiable as a novice, resulting in direct social engineering block attempts or malicious private messages to trick you into downloading malware, or revealing personally identifiable information for extortion at a later point. You move from a passive role to being an active participant in a criminal ecosystem.
9. Psychological and Emotional Trauma
The exposure to extreme violence, disturbing ideologies, politically extreme materials, or self-harming content can have extremely severe long-lasting emotional and psychological trauma. The content is unfiltered, uncensored, not just graphic; the content is intentionally shocking. There are no warnings.
As for the matrix of unregulated content online in the dark web, one cannot factor in how people are simply transmitting and opining about these topics. The unseen mental expense may be one of the most significant and overlooked disadvantages of dark web and its exploration.
Take, for example, minors or people who are naturally inclined to anxiety; emotional content can invade your psyche and can lead to intrusive thoughts or awareness that create severe emotional distress that might warrant additional psychological capacity.
10. Lack of Recourse and Reliability (Exit Scams and Service Failure)
The entire ecosystem operates on zero consumer protection. Every transaction and every service relies solely on the implicit anonymity and trust in the vendor, which is inherently unreliable. Exit scams, where an entire marketplace disappears with user funds and vendor deposits, are a recurring phenomenon.
Furthermore, paid services (like promised hacking or data acquisition) often fail to deliver, or the supposed seller simply takes the money and disappears. If you are scammed, your funds are gone forever. There is no authority, no refund policy, and no recourse to report the crime or recover losses, making all interactions high-stakes gambles.
Is the Dark Web Illegal?

One of the most misunderstood elements of the hidden internet goes into the question: Is the dark web illegal? The quick answer is – No; connecting to the dark web is usually not illegal; it’s what you actually do in the dark web that is.
- The Technology is Legal (Tor): The Tor network, itself, is just a method/tool for anonymous communication. It is a legitimate technology used daily by journalists, human rights activists, and government entities to communicate safely and bypass censorship. Using the dark web browser to access dark web sites is not, in itself, a crime in most democratic nations. The tool is neutral.
- The Activity is the Crime: The moment you use that tool to buy or sell illegal items (drugs, firearms, stolen credentials), download prohibited material, or solicit criminal services, you are committing a highly illegal act.
- Government Stance: Law enforcement globally maintains that using the Tor network is completely legal. However, they also dedicate massive resources to infiltrating the criminal sections of the network. Given the use of Tor by those committing illegal acts, the involvement with Tor could be viewed as further evidence in proving premeditation and intent to hide the illegal act, likely leading to a lengthier sentence.
The risk is not using the technology, but the likelihood of finding criminal activity to engage with when you reach the dark web.
5 Most Popular Dark Web Sites

The popularity of dark web sites is volatile, but they generally fall into clear categories based on their function. This list illustrates the diversity of the hidden web:
- Hidden Wiki
A legacy directory and index of .onion links. It serves as a necessary, but highly dangerous, starting point for navigation, often containing a mixture of informative and highly illegal links. OnionWiki is a safer alternative to many Hidden Wikis out there today.
- Darknet Markets (Awazon Market, AlphaBay Reloaded)
These are extensive, Amazon-like e-commerce sites focused on the sale of illegal goods, varying from drugs to counterfeit ID cards and records of stolen data. They are consistently the focus of global law enforcement takedowns. One that has become popular lately is Awazon (yes, it’s similar in name with Awazon).
- Secure Communication Services (ProtonMail, Riseup)
These are legitimate, privacy advocacy email and collaboration services that have .onion addresses, which allow users to feel secure, to an extent, from their content being metadata harvested and to help avoid government censorship.
- Whistleblowing Platforms (Such as SecureDrop)
These are platforms both for journalists (like ProPublica and The New York Times) to receive materials and information from anonymous sources and whistleblowers safely.
- Bitcoin/Cryptocurrency Tumblers/Mixers
Services that mix a user’s coins with other coins in a way that obscures the pathway on the blockchain, mostly used by those who belong to criminal organizations that mess with money laundering.
Curiosity Isn’t a Crime, but Carelessness Can Be Expensive
It’s only natural to be curious about the dark web, given all the sensationalistic stories and stories provided by the media. Being curious about an anonymous and hidden network is not against the law, but choosing to satisfy that curiosity without equipping yourself is extremely costly.
The moment a user clicks on a malicious link, enters personal information, or makes a mistake with some configuration and setting in the dark web browser without considering the implications, they cross the line between safe exploration and major compromise.
The costs associated with careless risks aren’t just identity theft and financial devastation – they seriously are the potential of being caught up in legal issues and psychological harm from the exposure to illegal content, like abusive sex videos. Your first mistake on the dark web will likely be your most expensive mistake.
Conclusion
Ultimately, what the discussions about the dark web center on is utility versus risk. It is clear what the Advantages and disadvantages of dark web access are: it can provide an indispensable refuge for people with a true need for anonymity (like journalists, political dissidents, and whistleblowers), but it can also provide a deeply hostile environment for the casual user.
The dark web dangers and risk are not a theory; dangerous consequences are indeed built into the design of the network. The very anonymity that gives a shield to the activist also gives a shield to the scammer and malware distributor.
For the lay person, the downside—high probability of malware, being scammed, or suffering severe psychological trauma from illegal and deviant content—vastly outweighs any potential upside. If you are a regular person without a compelling need to engage in the dark web space, your safest choice is not to even engage.
If you do need to engage in the dark web, just remember anonymity is a shield, not an impenetrable barrier. Your shield is only as strong as your own knowledge.
FAQs
Yes, the dark web is unsafe because it is a wholly unregulated environment that has a very high number of more sophisticated criminal actors than the visible web. The primary risks consist of malware, ransomware, and advanced phishing scams that can affect your whole system and steal your identity.
The dark web browser (the Tor browser) provides anonymity on its own but you should include a good VPN before connecting to the dark web. This is a practice called Tor over VPN. This technique also ensures that your ISP and the Tor Entry Node for your connection can’t see your real IP Address while connecting to the dark web, adding another layer of protection and defense against traffic analysis.
Yes. Although the dark web is relatively anonymous in a way, it is not invisible. Law enforcement is actively using advanced techniques, such as vulnerabilities in the dark web browser (the Tor browser) and looking at traffic patterns to track and de-anonymize users who are engaging in illegal acts.
The difference between the deep web vs dark web is intent. The deep web is any non-indexed content (i.e., private email, bank statements) and is legal. The dark web is the small part of the deep web that is purposely hidden and encrypted (Tor/I2P) to allow maximum anonymity and is usually used for illegal purposes.
