The dark web is one of the most elusive and misrepresented areas of the internet. While the mainstream media loves to deceitfully depict the dark web as the wild west and criminals are lurking at every turn, that is far from the truth. This comprehensive guide will unpack the dark web and explain what it is, how it works, and whether it is really as dangerous as it is portrayed to be by so many.
Whether you’re a curious observer, a privacy advocate, or you just want to understand a mysterious part of the web, we’ll share everything you need to know on this page.
We’ll discuss how the surface web differs from the deep and dark web, we’ll cover safety, the legalities of what you can see and find in these areas, and finally, for those who want to venture into these other parts of the Internet, we’ll discuss how to navigate these darker areas.
What is the Dark Web? (Explaining Dark Web, Deep Web, and Surface Web)
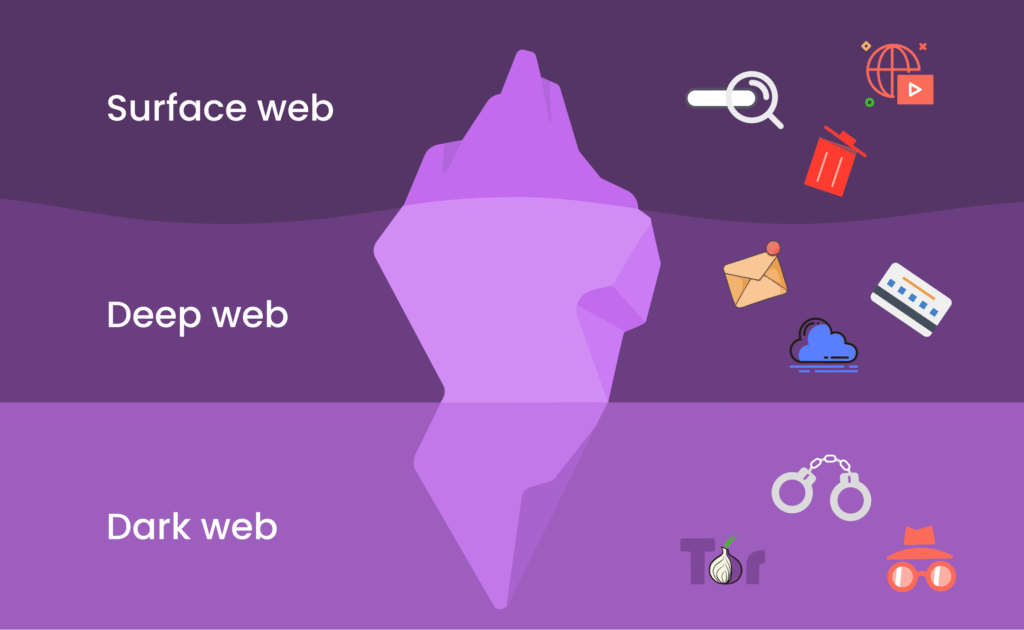
When you hear the word “Internet,” you probably think of only the URLs you can access from a quick Google search. But that is just a small, small portion of the entire network. To conceptualize what the dark web is, it can be helpful to visualize the entire Internet as an iceberg. This metaphor can be useful to illustrate the layers we know exist above the water, but also the many more layers that exist beneath the surface, which most people may not even realize are down there.
The Surface Web, or Open Web
The “surface web” or “open web” is the portion of the internet that can be viewed or accessed using search engines like Google and Yahoo. If we think of an iceberg, the open web is the tip above the water. The surface web accounts for less than 5% of the entire internet.
This is all of the common public-facing websites that you access via traditional browsers (Chrome, Firefox, Internet Explorer), all of which are typically via registry operators like “.com” or “.org”. Search engines access these websites through a process called “crawling,” which allows them to access visible links and traverse the web like a spider.
The Deep Web
Underneath is the “deep web”, which is the iceberg just under the water, that accounts for approximately 90% of all websites. The deep web is so large that we will never know how many pages or sites are working at any given moment. Think of search engines as fishing boats; whatever they are able to catch is whatever is nearest to the surface, and anything else is thrown back into the deep web.
The deep web is the collective of web pages that cannot be searched on the search engines. These pages are pretty much safe and legal, and you probably access these types of pages every day. Deep web pages usually require some sort of password or other gates to protect their information and the user’s privacy.
A few of the largest parts of the deep web are:
- Intranet: A private network used within organizations (companies, government, educational organizations) to communicate and manage operations in the private space. Generally, they use the general infrastructure of the internet, but on a private link.
- Databases: Publicly and privately protected file systems, where the files and pages are detached from the typical surface web parts. A database can only be searched from within it, like a library catalog system or medical record database.
- Content protected by a password: Your online banking pages, your secure social media sites, your email, and your subscription services are in the deep web.
- Unlinked content: These are pages of websites that have not been linked to the other areas of the websites, meaning they aren’t indexed by the search engines.
You probably use the deep web every day without even knowing it. When you sign in to your online banking, check your private email, or access your company’s internal systems, you are accessing deep web content. Much of this information is hidden for a number of legitimate reasons – user privacy, security, and confidential information.
The Dark Web
The dark web is a small part of the deep web and the absolute bottom of the iceberg. It is the most hidden part of the deep web, and most people will not ever touch it. The dark web is defined by its anonymity and can only be accessed using specific browsers that support anonymity, like Tor (The Onion Routing).
The dark web is a completely separate, hidden network built with a few features that allow it to be a completely anonymous haven:
- No search engine indexing: Search engines like Google cannot find and return results for dark web pages. This means that dark web pages exist completely disconnected from the surface web.
- Anonymous infrastructure: The dark web works through a randomized network infrastructure that creates “virtual traffic tunnels”. This makes it incredibly complicated to track down users or website operators.
- Special browser required: You cannot visit a dark website through a regular browser. You need specific software like Tor (The Onion Router) in order to use these hidden services.
- Unique addressing system: Dark web sites use the .onion domain extension, instead of traditional domains, and addresses like “5guruk3zcpgvr7wh.onion” that appear as random letters and numbers.
Dark websites are often associated with illegal activities, and while those sites are definitely there (especially if you know where to look), there are some legitimate purposes that the dark web can serve.
Journalists, activists, whistle-blowers, and people living under tyrannical regimes use the dark web to communicate safely and access information without surveillance and retribution.
How to Access the Dark Web Safely?
Accessing the dark web isn’t like strolling through a park. It can be a dangerous place with lots of threats, and if you hit the wrong link, you could expose yourself, your money, or your device.
If you need to access the dark web, here is a quick and safe way:
1. Get a Good VPN
Before you do anything else, link to a good VPN (NordVPN, Surfshark, etc.). A good VPN will mask your IP, encrypt your traffic, and prevent your ISP from looking over your shoulder.
2. Download the Tor Browser (from the Official Website)
Make sure you get Tor from the Tor Project. The Tor Browser routes your internet traffic through encrypted relays, making it difficult to track your activity.
3. Try TAILS OS
TAILS runs from a USB stick and allows you to forget everything when you turn it off – great for ensuring you leave no trace whatsoever. The TAILS OS comes with Tor pre-installed.
4. Use Layers of Protection – VPN Over Tor
If you want to protect your anonymity as much as possible, link to your VPN, then fire up Tor. It will be slow, but much more difficult to trace. Use VPN providers with:
- No-Logs Policy
- Crypto payment options
- Obfuscation (makes VPN use undetectable)
- Good encryption, good speed
5. Only Use Cryptocurrency for Payment
Do not use any credit cards. Use privacy coins like Monero or Zcash, or, at the very least, mix your bitcoin to obfuscate it.
6. Exercise Additional Caution
Close any other apps before running Tor, disable any unnecessary services, and cover your webcam. The more avenues of attack that an outsider can exploit, the more risks you will run.
7. Understand Where You are Going
Utilize trusted directories of the dark web, as this will assist you in avoiding malicious or watched sites. If it does not feel right, stop and back out.
8. Shut Down Everything When Done
Make sure you exit from the Tor application, shut down TAILS (or reboot your operating system), and make sure nothing else is still running in the background.
What is Really on the Dark Web?

The dark web thrives on privacy and anonymity—but along with privacy dark web also has innocent spaces or completely illegal markets. While we might come across puzzle sites or niche eBooks for sale, all of its notoriety comes from what is being exchanged in the darkness.
Here is just a taste of what is out there:
- Drugs & hazardous chemicals: From marijuana to hard drugs, plus hazardous chemicals that have the ability to harm.
- Stolen data & counterfeit IDs: Bulk credit card numbers, social security data, hacked streaming accounts, and even fake passports.
- Black-market services: This includes human trafficking, counterfeit goods, mercenaries for hire, or other disturbing items.
- Weapons & explosives: Things like rocket launchers, C4, small arms – usually paid for in cryptocurrency.
- Hazardous materials: You could see even uranium ore for sale.
- Deadly poisons: Deadly substances like ricin, usually glamorized in pop culture but deadly in the real world.
- Fake credentials: counterfeit diplomas and professional credentials.
- Malware & hacking tools: viruses, ransomware kits, phishing services.
- Scams: Many “hitman” services and ridiculous offerings are just scams, designed to steal money or data.
Legal applications: For many, this is a tool for freedom and safety. Victims of abuse, whistleblowers, and dissidents often use these hidden sites to communicate without the fear that their identity will be exposed. Citizens living under strict censorship laws use the dark web to bypass government bans and access information and communication freely.
Illegal applications: The same anonymity that protects whistleblowers also provides a shelter for criminals. Cyberattacks, trafficking of illegal goods and services, and the sharing of illegal content are all frequently accepted behaviors. The dark web hosts illegal marketplaces where members can buy everything from stolen personal data to weapons and drugs.
Is Using the Dark Web Illegal?
No, in simple terms. Using the dark web is not illegal – the legality of your conduct depends on your use of it. The dark web is in the gray area – it is a mechanism that can be used for legal and illegal conduct.
Is Tor Illegal to Use?
Tor and other anonymized browsers are not particularly illegal. In fact, these tools are not exclusively used to access the dark web at all. Many people use Tor as a legal means to surf the public internet privately. These people consider the usage of Tor a protection from Private corporations and their spying mechanisms, as well as government spies.
Also, the availability and use of Tor is maintained in countries with hard censorship laws. But using a legal browsing tool does not mean that your actions are legal. Authorities can still charge you with crimes if you use Tor to host copyrighted material illegally, share illegal pornography, or engage in cyberterrorism.
Is the Dark Web Illegal to Use and Visit?
Simply browsing the dark web online is not illegal, but a lot of the dark web is rife with disgusting behavior, so be kind to yourself. If something is illegal in your place of jurisdiction, then it is still illegal if you do it while you are on the dark web. Criminals and malicious hackers especially prefer to operate maliciously. For this very specific reason, it is not a space to be taken lightly because being there can make you vulnerable to avoidable exposure if you’re not paying attention.
Types of Threats on the Dark Web

The anonymity of being on the dark web can be a benefit, but it also has serious consequences.
Here are some of the most common threats you may experience while browsing the dark web:
- Malicious Software: The dark web is an environment to mass-produce malicious software or “malware”. Portals regularly offer it to threat actors as tools for cyberattacks, and it also lurks there to maliciously infect unsuspecting users—just as it does across the rest of the web.
- Key loggers: These programs record your keystrokes, allowing an attacker to steal your passwords and other valuable data.
- Botnet malware: This malware can turn your computer into a “bot” that could be in a network of sockets run by an attacker.
- Ransomware: This malware locks your files and requires a ransom to let you decrypt them.
- Phishing malware: This form of malware is used to conduct phishing scams in order to get you to tell them personal information.
- Government Surveillance: The dark web is not a black hole. Police and security agencies around the world actively surveil and infiltrate websites under Tor. Agencies have hijacked illegal drug marketplaces such as the Silk Road to surveil the websites. Law enforcement infiltrates dark websites to capture the identities of users, including both patrons and bystanders. Even if you don’t purchase anything and only browse, they can place you on a watchlist and use you in a future investigation.
- Scams: The anonymity that the dark web provides makes it rife with scams. There are well-known threats that utilize the dark web to find their victims; they parade as harmful, subversive, or illegal activity in order to exploit the negative reputation of the dark web.
Furthermore, there have been reports of scams regarding services offered on the dark web that do not exist. One example of this false service is a “professional hitman.” Other times, attackers use phishing scams to steal your identity for future extortion purposes.
Ways to Safeguard Yourself from Dark web Exploitation
Preventing threats originating from the dark web is not just about avoiding shady websites. Unfortunately, attackers can victimize you even if you never approach the dark web.
Perpetrators will frequently collect stolen information from hidden marketplaces on the dark web and then use that stolen information in very mundane ways, like perhaps fake calls from your “bank,” other phishing emails, etc., or turning on a credit card charge in your name.
The best protection? A layered defense that will look after your identity, protect your finances, protect your devices, and take mitigation measures in your everyday web browsing.
1. Protect Your Identity
Your personal data can appear on the dark web even if you didn’t do anything. Say you were a part of a retail hack, a hospital hack, or even hacked personal data from government databases (e.g., employee databases).
Here’s what you can do:
1. Engage an identity monitoring service and activate it. Identity monitoring services search through dark web marketplaces and dark web breach dumps for your personal data.
2. Set alerts for findings of specific data, to protect your identity, such as:
- Social Security or national ID numbers.
- Bank and credit card numbers.
- Emails and passwords.
- Home address and phone number.
- Medical record or driver’s licence number.
3. Take action immediately if you find your details. Change your passwords, notify your banks, and create fraud alerts first, before the bad actors act.
2. Treat Your Money Like a Hawk
The bad guys can monetize stolen financial details with ease on the dark web. They could drain your bank accounts, rack up charges on your credit, or even create new credit in your name, without you knowing.
Use these steps to protect yourself:
- Enable fraud monitoring for all your bank and credit accounts. Most banks will notify or text you as soon as suspicious activity appears on your account.
- Freeze your credit with all the credit bureaus. It’s free, and you can always just temporarily lift it when you actually want new credit.
- Use complicated and unique passwords for every financial account—and save them in a password manager.
- Enable two-factor authentication wherever available, reiterating the benefits of adding another lock to your front door.
3. Fortify Your Devices
Links to bad sites aren’t the only threats; dark web sources can spread malware through compromised ads, email attachments, or downloads.
When searching for security software, don’t just look for an antivirus. Choose a security suite with:
- Real-time scanning for websites and files.
- Behavioral protection for new threats.
- Monitoring your network for questionable connections.
- Filtering emails for phishing attempts.
- Automatic updates to protect against the latest exploits.
Keep your software updated, conduct regular scans, and let it worry about finding trouble before it lands.
4. Browse Smart – Anywhere
You can inadvertently download malware from compromised “normal” sites. Safe browsing habits are your ongoing line of defense.
- Think before you click. Avoid links in urgent emails or social posts with “exclusive” offers.
- Stay updated. Update your operating system, browser, and plug-ins. Unpatched software is an invitation to hackers.
- Use reputable sites for shopping or banking, and check for HTTPS before entering payment info.
5. Have a Breach Response Plan
If a breach compromises your data, your quick action can decide whether it becomes a nuisance or a catastrophe.
Your plan should include:
- Change the passwords right away for any accounts you suspect are involved.
- Call your bank or credit card issuer and inform them you are concerned about fraudulent activity.
- Put a credit freeze or fraud alert on your accounts to halt any new accounts being opened in your name.
- Keep a log of everything you do – this will be an excellent resource for disputes you might face, or for insurance purposes.
- Monitor your accounts closely for the months to come.
Helpful tip: Keep your financial institutions’, credit bureaus’, and monitoring service’s contact numbers easily accessible so you don’t get caught off guard.
How to Stay Safe While Using the Dark Web
If you are going to venture into the dark web, you might want to seriously consider the following tips so that you can stay safe:
- Use a VPN: A VPN allows you to hide your IP address and online activity. Reviewers consistently rate VPNs like NordVPN among the best, and the service offers double encryption (double-VPN) to give you extra safety and maximum anonymity.
- Don’t make any purchases: We do not recommend you purchase anything from the dark web. Most of the purchases you can make are risky and scams, even when they appear to be authentic. You will most likely lose money or expose yourself to the dangers of hackers.
- Use a quality antivirus: Antivirus software, like TotalAV, can go a long way in keeping you and your device safe from potentially harmful downloads or viruses.
Download the Tor browser and modify your default Tor settings for maximum privacy. Turn off ActiveX, JavaScript, and Flash plugins, but remember that most dark websites won’t work properly without them.
Be cautious when it comes to downloads. Downloading things on the dark web is dangerous, as you can download the wrong file among the abundance of false files.
Conclusion
In this guide, we’ve explored the three levels of the internet: the surface web, the deep web, and the dark web. The dark web, although small, is a unique and complex area of the internet that provides both a unique sanctuary to communicate privately, along with a breeding ground for danger and threats. People use this tool for legitimate purposes to shield their identity from surveillance and censorship.
On the flip side, the dark web poses significant risks. By knowing how the dark web works and following the safety guidelines in the guide above, you can protect your personal information and navigate the digital world more securely. Did this guide help you understand the dark web better? If so, please share with someone you think may find it useful, and comment below if you have questions. We will gladly answer them!
FAQs
It is not correct to use the verb “create” in discussing the dark web. The principal technology used to access the dark web, Tor, was developed in the mid-1990s by the United States Naval Research Laboratory to help protect U.S. intelligence communications. Eventually, this technology was repurposed and released to the public.
Tor stands for “The Onion Routing”. It is a free, open-source web browser that allows users to use the web anonymously. Instead of the default direct order, the Tor browser will drag your traffic around a nonsensical path of encrypted servers called “nodes,” which hides your identity and browsing history.
The deep web is the massive portion of the internet that cannot be indexed by search engines, such as private databases, online banking, and email accounts. The dark web is a small part of the deep web that must be accessed with a special browser like Tor, which is anonymous.
Yes, there are search engines for the dark web. Since it is not indexed by traditional ways or curated through Google, there are search engines specifically designed to find the .onion sites. They are usually not as thorough and reliable as surface web search engines.
There are dark web monitoring services out there that can check your data on the dark web for you, such as email addresses, passwords, and credit cards. Many of these services are included in comprehensive internet security suites.

